Liquity v2 ~ Governance (3rd audit)
Smart Contract Security Assessment
December 22, 2024
Fixes (4th) Re-Audit: January 17,2025

SUMMARY
ABSTRACT
Dedaub was commissioned to perform a 3rd security audit of the Liquity v2 Governance protocol. Dedaub has previously been commissioned to audit two earlier versions of the codebase, the reports of which can be found at (Liquity v2 ~ Governance (1st audit) - Aug 12, 2024) and (Liquity v2 ~ Governance (2nd audit) - Nov 11, 2024). In these previous versions, one important issue was the rounding errors caused by how the average timestamps were calculated. In the current version, the voting power mechanism was refactored to eliminate the rounding issues. This review considered the codebase in its entirety and not only the delta of the changes between the current and the previous versions.
The code has improved even more in several important parts compared to the previous versions and has also been simplified in several complex parts. However, some of the reported issues remained active and some new ones were found.
The test suite was also extended with more test cases to better cover the most important parts of the protocol. We highly recommend more extensive unit tests to cover complex and edge case scenarios of the protocol.
After the fixes review, the codebase was further improved addressing the rounding errors in various components of the protocol. Some new assumptions were made and the protocol’s specification was updated to reflect them properly. The test suite was also extended and most of the issues were resolved.
BRIBE DISTRIBUTION FORMULA ANALYSIS
The current version of the codebase introduced further changes in the formulas used to calculate and distribute the bribes to the eligible users in the BribeInitiative implementation as well as to calculate and distribute the user’s allocations over a set of initiatives in Governance::allocateLQTY implementation. The new formulas aim to account for the rounding errors that the previous mechanism had.
Below we provide a thorough explanation of the new formulas and proofs for their correctness and fairness for all the users. We perform the analysis for the formula to calculate the bribes but the same analysis can be applied for vote allocation.
Let be the amount of bribe remaining to be distributed after the user claimed his bribe, be the amount of votes of the user, be the total amount of votes, and is the total amount of bribe to be distributed.
Notice that:
Therefore,
Fact 1: If , then for all possible values of and
Proof:
Fact 2: If , no undistributed bribes can remain due to rounding errors
Proof:
So, the computation of does not require any floating point arithmetic.
Fact 3: If , then the system is fair
Fairness Definition:
For every ,
Proof:
Let us show that for every , ,
for :
for :
Now suppose that:
for :
So by induction, for every i,j, .
Therefore, and thus the system is fair.
Rounding errors for each user
Let be the rounding error for the remaining bribes to be distributed. By definition, , and as proved above . Note that the rounding error for the bribe of each user is the same as the rounding error for the remaining bribes to be distributed.
for :
for :
for :
We can clearly see that for all . Additionally, we can find an upper bound for as follows:
The highest error happens for where
SETTING & CAVEATS
This audit report mainly covers the contracts of the repository liquity/V2-gov of the Liquity v2 Governance Protocol. The audit was based on PR #97 at commit d11e15a11ebdb26c7b297572d9674a7801f50922.
Two auditors (along with 2 junior auditors) worked on the codebase for 5 days on the following contracts and 2 extra days for reviewing the fixes:
- BribeInitiative.sol
- CurveV2GaugeRewards.sol
- ForwardBribe.sol
- Governance.sol
- UniV4Donations.sol
- UserProxy.sol
- UserProxyFactory.sol
- interfaces/
- utils/
As part of the audit, we also reviewed the fixes of the issues included in the report. The fixes were delivered in separate PRs which had already been merged by the time the re-audit started. Hence, the review of the fixes was based on the diff between the audit’s base commit (d11e15a) and the at-the-time latest commit of the main branch (68b7110) and we found that they have been implemented correctly:
-
PR #107 · fix: wrong calculation of the bribes given to each user
(merged inmainat commit90d02b5ab3252e16106b9ec06c9451b23bcafd5b)
Addresses issue H1 -
PR #120 · chore: fix incorrect or outdated comments by danielattilasimon
(merged inmainat commitb5ade69b7ea51db8353544e7b0a31b76b618a5e4)
Addresses issue H3 -
PR #126 · feat: don't call
onAfterAllocateLQTY()on vetos
(merged inmainat commit1c379b59f184f5805cf851d3969c6d0f800626b1)
Addresses issue M1 -
PR #114 · fix: registration fees go to previous epoch
(merged inmainat commitaa5a7705f82968da8ae84efb7a2e880fe7e8705d)
Addresses issue M2 -
PR #123 · fix: dust left after claiming all bribes
(merged inmainat commitf6839c9d80e0622ef5a0ea5ae3af3070872c1c52)
Addresses issues M4 and partially M5 -
PR #121 · refactor: remove stale and redundant check
(merged inmainat commitffbf480150d08feea02036a31c9b67119a4c2685)
Addresses issue A2 -
PR #110 · Reset no longer needed on staking & fix underflow
(merged inmainat commitb5ab005ecb2ae15c63d9444dc079f2257c03039d)
Addresses issue A6 and A8
The audit’s main target is security threats, i.e., what the community understanding would likely call "hacking", rather than the regular use of the protocol. Functional correctness (i.e. issues in "regular use") is a secondary consideration. Typically it can only be covered if we are provided with unambiguous (i.e. full-detail) specifications of what is the expected correct behavior. In terms of functional correctness, we often trusted the code’s calculations and interactions, in the absence of any other specification. Functional correctness relative to low-level calculations (including units, scaling and quantities returned from external protocols) is generally most effectively done through thorough testing rather than human auditing.
PROTOCOL-LEVEL CONSIDERATIONS
The current version introduced the logic of enforcing the reset of the users’ allocations every time they want to update them. In addition to that, in Governance::allocateLQTY checks were added to ensure that each Initiative has been provided only once and no double processing could be done for the same address. However, both the resetting and the reallocation invoke the Initiatives’ onAfterAllocateLQTY hook. This means that during a single allocation the hook can be called twice for the same address, possibly breaking the implemented checks in an Initiative.
The new resetting mechanism enforces the users to reset all their allocations before updating their allocations. When resetting, the Governance::_allocateLQTY function invokes the onAfterAllocateLQTY hook on the Initiative.
However, if time sensitive Initiatives existed in the future, which may depend on the timestamps at which the users voted or vetoed for their reward or bribe distributions, resetting and reallocating the users’ votes can inherently affect their accounting and make users lose or get more rewards than supposed to.
The existing BribeInitiative template and the example applications (CurveV2Gauge, UniV4Donations and ForwardBribe) are not time sensitive, but since the protocol aims to support any arbitrary contract as an Initiative, such scenarios are not unlikely to exist.
VULNERABILITIES & FUNCTIONAL ISSUES
This section details issues affecting the functionality of the contract. Dedaub generally categorizes issues according to the following severities, but may also take other considerations into account such as impact or difficulty in exploitation:
- User or system funds can be lost when third-party systems misbehave.
- DoS, under specific conditions.
- Part of the functionality becomes unusable due to a programming error.
- Breaking important system invariants but without apparent consequences.
- Buggy functionality for trusted users where a workaround exists.
- Security issues which may manifest when the system evolves.
Issue resolution includes “dismissed” or “acknowledged” but no action taken, by the client, or “resolved”, per the auditors.
CRITICAL SEVERITY
[No critical severity issues]
HIGH SEVERITY
Resolved
In the hook function BribeInitiative::onAfterAllocateLQTY, the offset of the user's allocation is taken from _userState.allocatedOffset instead of taking it from _allocation.voteOffset. The value _userState.allocatedOffset corresponds to the offset for all LQTY allocations made by the user (for all initiatives the user voted to). This leads to a wrong calculation of the number of votes from a user for the bribe Initiative. In particular, _userState.allocatedOffset is always greater than or equal to _allocation.voteOffset. So, the user's votes for the initiative will be undervalued (larger offset means less votes) and thus, the user receives fewer bribes than he should. Even worse, the amount of bribes that the user could not claim, due to the bug, remains stuck in the bribe Initiative as no user can claim them. One detail to mention here is that the bug is a race condition based on the position of the bribe Initiative address in the array of initiatives passed by the user to Governance::allocateLQTY function. Having the bribe initiative further in the array leads _userState.allocatedOffset to accumulate more offsets from the other Initiatives’ allocations resulting in a larger value than _allocation.voteOffset and consequently more bribes lost.
BribeInitiative::onAfterAllocateLQTY:232function onAfterAllocateLQTY(
uint256 _currentEpoch,
address _user,
IGovernance.UserState calldata _userState,
IGovernance.Allocation calldata _allocation,
IGovernance.InitiativeState calldata _initiativeState
) external virtual onlyGovernance {
...
// Dedaub:
// Should use _allocation.voteOffset instead of
// _userState.allocatedOffset
_setLQTYAllocationByUserAtEpoch(
_user,
_currentEpoch,
_allocation.voteLQTY,
_userState.allocatedOffset,
mostRecentUserEpoch != _currentEpoch
);
}
A sample demonstration of the bug can be seen in the following scenario:
-
Given a bribe initiative
bribeInitiative1that has amount of bribes deposited for epoch and two users with some large amount of LQTY deposited at . -
Epoch n:
user_1allocates LQTY forInitiative2and another LQTY for initiativebribeInitiative1by callingallocateLqty([], [Initiative2, bribeInitiative1], [x,y], [0,0]).This call triggers the hook ofbribeInitiative1.onAfterAllocateLQTY()with (the correct offset should be ). -
Epoch n:
user_2allocates LQTY forbribeInitiative1. -
Epoch n+1: Both users claim their bribes for epoch
nby callingclaimBribes({n, n, n}).user_1receives anduser_2receives . This results inuser_1losing of his bribe which gets stuck inbribeInitiative1forever as no one can claim them.
MEDIUM SEVERITY
Partially resolved
onAfterAllocateLQTY hook on vetos to prevent any voting manipulation. The alternative expressions of the issue were acknowledged by the team.For voting to be fair, it is important that both positive and negative votes have similar costs. Apart from the cost in terms of voting power obtained by staking, we should also consider the actual gas cost of executing the voting transaction. However, the gas cost can be manipulated by a malicious user to make vetos substantially more expensive than votes, exploiting two aspects of the voting design:
-
Every call to
allocateLQTYcalls theonAfterAllocateLQTYwhich is controlled by the adversary. -
allocateLQTYrequires resetting all previous votes and re-casting them, which essentially means thatonAfterAllocateLQTYwill be called times for every voting operation, where is the number of previously voted Initiatives. -
Now consider a malicious user submitting Initiatives whose
onAfterAllocateLQTYconsumes all available gas in case of a veto, but a tiny amount of gas in case of a vote. Even though the gas is capped byMIN_GAS_TO_HOOK, the current value of350.000is large enough to allow a substantial manipulation. With a gas cost of20 Gwei(not uncommon), calling the hook alone currently costs around$18. There is a scenario in which an adversary can submit such Initiatives and make the total hook calls when casting vetos for all of them to be which is equal to . With10malicious Initiatives we need$1800just to call the hooks (not counting the cost ofallocateLQTYitself). -
The idea is that the adversary submits the Initiatives on different epochs and votes for them so that they become eligible to get rewards or just stay active in the system for as long as required (for simplicity we do not consider the warm-up periods and similar mechanisms, as they do not directly affect the scenario).
-
On
epoch_a, the first malicious Initiative becomes active for voting and the users veto it paying the expensive hook call once. -
On
epoch_b > epoch_athe adversary’s 2nd Initiative becomes active and the users veto this as well, but also keep their vetos active for the 1st malicious Initiative. Thus, they pay they will have to pay2 + 1times the expensive hooks since they have to reset all their allocations (1 call) and reallocate them back (1 callveto of the 1st Initiative) along with their new allocations (1 callveto for the new (2nd) Initiative). -
As can be seen, each new Initiative requires calls to the expensive hooks resulting in the quadratic cost.
-
Since
1Initiative becomes active every epoch, otherwise if all of them were in the same epoch the users could veto them at once and avoid the quadratic cost, the complexity could be also expressed in epochs and be where is the number of epochs passed.
Alternative Expressions of the Issue:
The direct manipulation of the vetos could be deemed as the most important, but other expressions of the issue also exist that could be used to manipulate specific execution paths. For example:
-
Users who have voted for an Initiative that turned out to be malicious or compromised could experience the same issue. Malicious Initiatives detecting vote reduction could similarly treat it as vetoing and consume all the available gas making the hooks expensive.
-
Similarly, every resetting operation that even temporarily zeros all the votes before the reallocation could also be used to abuse the system. Any voted malicious Initiative could make any resetting operation quite expensive.
-
As a side effect, the vote removal from unregistered Initiatives (as described in L2) could also be used to make the deallocation unfair and expensive for the users who wish to remove their votes from the inactive Initiative.
Resolved
In the Governance contract, every time an epoch changes, calls to _snapshotVotes update the global state including the boldAccrued which stores the amount of BOLD tokens to be distributed among the Initiatives that became CLAIMABLE in the previous epoch.
Governance::_snapshotVotes:297function _snapshotVotes() internal returns (
VoteSnapshot memory snapshot,
GlobalState memory state
) {
bool shouldUpdate;
(snapshot, state, shouldUpdate) = getTotalVotesAndState();
if (shouldUpdate) {
votesSnapshot = snapshot;
uint256 boldBalance = bold.balanceOf(address(this));
boldAccrued = (boldBalance < MIN_ACCRUAL) ? 0 : boldBalance;
emit SnapshotVotes(snapshot.votes, snapshot.forEpoch);
}
}
However, if we assume that the very first operation of the current epoch is an Initiative registration, the BOLD tokens paid as registration fees will be used by _snapshotVotes and will be considered as part of the rewards for the previous epoch. This happens because, inside the registerInitiative function, the fees are transferred to the contract before the snapshots are taken.
Governance::registerInitiative:477function registerInitiative(
address _initiative
) external nonReentrant {
// Dedaub:
// The registration fee is transferred before accruing the BOLD tokens
// for the current epoch
bold.safeTransferFrom(msg.sender, address(this), REGISTRATION_FEE);
require(_initiative != address(0), "Governance: zero-address");
// Dedaub:
// This function calls _snapshotVotes which updates the accrued BOLD
// based on the current balance of the contract
(InitiativeStatus status,,) = getInitiativeState(_initiative);
require(status == InitiativeStatus.NONEXISTENT,
"Governance: initiative-already-registered");
address userProxyAddress = deriveUserProxyAddress(msg.sender);
(VoteSnapshot memory snapshot,) = _snapshotVotes();
UserState memory userState = userStates[msg.sender];
...
}
The snapshots should always be the first operation of functions that update the state to ensure that the previous epoch has been properly concluded before any updates for the current epoch are applied.
M3
Race condition could prevent users with sufficient voting power from registering new Initiatives
Acknowledged
For a user to be able to register a new Initiative, they need to pay a flat fee of 100 BOLD tokens and have a voting power greater than a percentage of the total positive (“YES”) votes that all the existing Initiatives have gathered. This was done to prevent system abuse by spamming Initiative registrations as the Governance::registerInitiative function is permissionless.
However, even if a user has sufficient voting power to register an Initiative, there exists a race condition in which they can be blocked from registering following the scenario below:
-
The user has staked enough LQTY in a previous epoch such that their voting power before the start of the current epoch surpasses the registration threshold.
-
In the running epoch, the user stakes an amount of LQTY that increases their offset (
newUserOffset). -
Then in the same block, the user tries registering a new Initiative. Following the invariant that when a user stakes more LQTY their voting power at that exact moment remains the same, the user should still be able to perform the registration operation.
-
However, this does not happen as the voting power calculation uses the
epochStart()to calculate the user’s offset. -
As a result, since
totalUserLQTY * epochStart() - newUserOffset < Voting threshold, the user is not able to register a new initiative.
A demonstration of the problem above can be seen in the following graph:
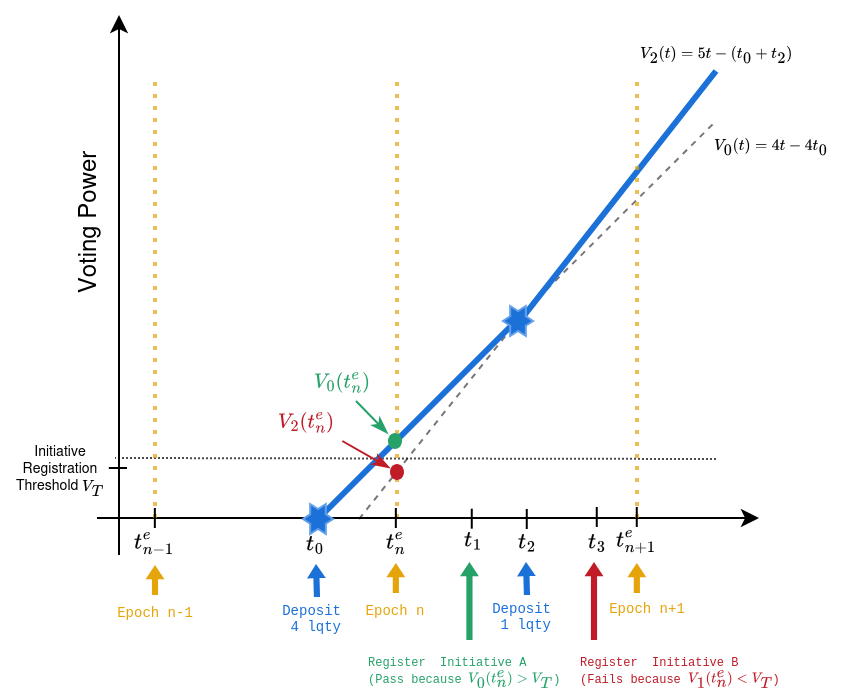
In this scenario, the user deposits 4 LQTY at . The user’s voting power is . Now in the next epoch (), if the user wants to register a new initiative his voting power allows him to do so because .
Now consider that the user deposits 1 more LQTY at in the same epoch. The user’s new voting power changes to . After this deposit the user cannot register a new initiative because .
Governance::registerInitiative:506function registerInitiative(address _initiative) external nonReentrant {
...
uint256 upscaledSnapshotVotes = snapshot.votes;
uint256 totalUserOffset =
userState.allocatedOffset + userState.unallocatedOffset;
require(
lqtyToVotes(
stakingV1.stakes(userProxyAddress),
epochStart(),
totalUserOffset
)
>= upscaledSnapshotVotes * REGISTRATION_THRESHOLD_FACTOR / WAD,
"Governance: insufficient-lqty"
);
...
}
In the first version, the require statement above used the block.timestamp, but this was changed to epochStart() as part of the changes in the previous version.
Resolved
In BribeInitiative, the claimBribes function was adjusted to help mitigate rounding errors in the average timestamp calculations from Governance. The last user to claim their bribes may be eligible for more rewards than the existing funds in the contract due to those errors and the function was made so that it adjusts the amount to be given according to the available balance expecting that only the user’s funds will be available.
BribeInitiative::claimBribes:129function claimBribes(
ClaimData[] calldata _claimData
) external returns (uint256 boldAmount, uint256 bribeTokenAmount) {
for (uint256 i = 0; i < _claimData.length; i++) {
...
(uint256 boldAmount_, uint256 bribeTokenAmount_) =
_claimBribe(...);
boldAmount += boldAmount_;
bribeTokenAmount += bribeTokenAmount_;
}
if (boldAmount != 0) {
// Dedaub:
// This adjustment is not sufficient to prevent the last user
// from claiming the excessive amount of rewards that may
// originate from the rounding errors of Governance as more
// BOLD tokens may exist in the contract
uint256 max = bold.balanceOf(address(this));
if (boldAmount > max) {
boldAmount = max;
}
bold.safeTransfer(msg.sender, boldAmount);
}
if (bribeTokenAmount != 0) {
uint256 max = bribeToken.balanceOf(address(this));
if (bribeTokenAmount > max) {
bribeTokenAmount = max;
}
bribeToken.safeTransfer(msg.sender, bribeTokenAmount);
}
}
However, this assumption is not always valid as anyone could have deposited more tokens for future bribes inflating the available balance. Moreover, the Initiative could have also claimed their rewards from Governance which would have increased the BOLD balance. As a result, the user’s amount will not be adjusted down as it should, but the amount with the rounding errors will be transferred consuming funds originating from other sources.
Acknowledged
EPOCH_VOTING_CUTOFF period, during which they should refrain from depositing more LQTY or keep their allocations unchanged if they deposited should they want to keep their voting weights the same.In the Governance contract, the new offset mechanism is used to account for various issues caused by the average timestamps of the previous versions. When a user stakes LQTY their state gets updated in the following way:
Governance::_increaseUserVoteTrackers:157function _increaseUserVoteTrackers(
uint256 _lqtyAmount
) private returns (UserProxy) {
...
// update the vote power trackers
userState.unallocatedLQTY += _lqtyAmount;
userState.unallocatedOffset += block.timestamp * _lqtyAmount;
...
}
As can be seen, the offsets encode both the staked amount and the staking timestamp which could alternatively be interpreted as the offset encapsulating the idea of the average timestamps, but in a way that does not introduce the rounding errors of the previous versions.
The following describes the behaviour of the new offset mechanism:
-
A user deposits amount of LQTY at which initializes their offset to the value of .
-
Later at timestamp and during the same epoch, the user deposits more LQTY. For simplicity, assume that , where some random elapsed time such that remains in the same epoch and .
-
The value of represents the virtual average timestamp embedded in the offset calculations. After the first deposit, the offset included the timestamp which was moved to after the second deposit.
Assuming the above, consider the following scenario which could make users experience more complexity in their interactions or even degradation in their allocations:
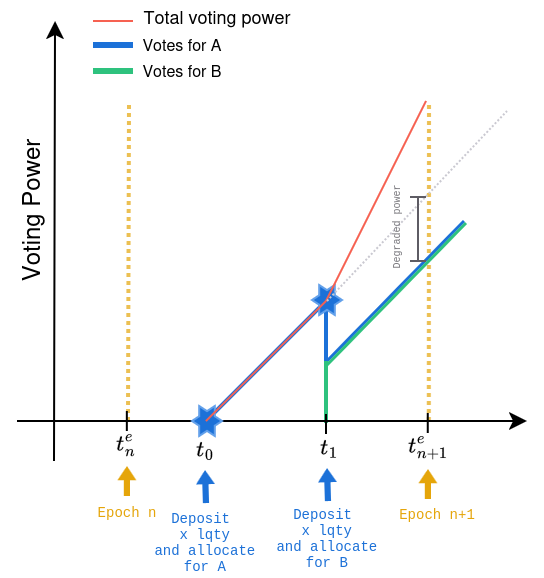
-
At the time of the first deposit (), the user allocates all their staked LQTY () on
Initiative_A. This means that the Initiative’s offset becomes: . -
At a later point in time (), the user decides to stake more LQTY, as described above, moving their offset to the value of: .
-
At the time of the second deposit (), the user allocates their remaining LQTY () on
Initiative_B. For this process, the protocol requires the user to deallocate all their existing allocations and then re-allocate them back along with the new allocations (this is enforced to account for some broader issues caused by users who (de)allocated their LQTY after depositing or withdrawing affecting their average timestamps and their voting power). -
However, after the user’s second deposit, their voting weight has been uniformly distributed over the new staked LQTY balance which is . This means that when the user allocates back the first LQTY to
Initiative_A, it will not receive the same voting power as before because the user’s offset has been increased leading to a degraded voting weight for the same amount of LQTY.
For the above scenario to be prevented, the users should be aware of this property and keep track of their allocations and their staking operations so that they can adjust the LQTY amounts re-allocated to the Initiatives after a new deposit so that they give them the same voting weight as before by increasing the allocated LQTY for those Initiatives which nevertheless introduces some more complexity on the user’s side. For example, in the previous scenario, the user needs to allocate for Initiative_A to preserve the same voting power at the end of the epoch (at ).
However, there is also a case in which the users cannot rebalance the difference as it becomes impossible to adjust their allocations. This happens during the EPOCH_VOTING_CUTOFF period, in which they are only allowed to allocate back to the Initiatives up to the amount they had previously allocated. This prevents them from distributing their new voting weight so that they do not degrade their votes from previously voted Initiatives, which nevertheless can make them lose part of their bribes due to the degraded votes.
Resolved
According to the defined specification the invariant that an Initiative can be unregistered if it has been stale (i.e. in a SKIP state) for more than UNREGISTRATION_AFTER_EPOCHS epochs is not followed. For example, in the following scenario a non-stale Initiative can become UNREGISTERABLE:
-
Assume that
UNREGISTRATION_AFTER_EPOCHS = 4. -
Epoch 1 - 2: Initiatives cannot yet be registered.
-
Epoch 3: Assume an Initiative has just been registered.
-
Epoch 4: The Initiative exits the warm-up period and becomes eligible for voting.
-
Epoch 6:
UNREGISTRATION_AFTER_EPOCHS - 1epochs have passed, since the warm-up period ended, with the Initiative not receiving sufficient votes to becomeCLAIMABLEin any of the previous epochs rendering it stale during that period. -
Epoch 7: In this epoch, it finally receives enough votes to become
CLAIMABLE. If it had not been voted for during this epoch, the Initiative would have becomeUNREGISTERABLE,as expected. -
Epoch 8: In this epoch, the Initiative is
CLAIMABLE, but let’s say its rewards are not claimed. This means that the rewards will be reused and Initiative’slastEpochClaimwill remain0. Moreover, during this epoch, all voters remove their votes from the Initiative so that it is no longerCLAIMABLE. -
Epoch 9: Now the Initiative can be immediately unregistered since
lastEpochClaim + UNREGISTRATION_AFTER_EPOCHS < epoch() - 1 ⇔ 0 + 4 < 7 - 1 ⇔ 4 < 6. However, this breaks the invariant of unregistration since the Initiative was not stale forUNREGISTRATION_AFTER_EPOCHSconsecutive epochs as it wasCLAIMABLEin the previous epoch.
LOW SEVERITY
In the BribeInitiative contract, the _claimBribe function was changed so that it supports the new offset mechanism for calculating each user’s voting contribution. Following these changes, the epochEnd variable was introduced to hold the value of the timestamp at which the epoch that we are claiming for ended.
BribeInitiative::_claimBribe:102function _claimBribe(
address _user,
uint256 _epoch,
uint256 _prevLQTYAllocationEpoch,
uint256 _prevTotalLQTYAllocationEpoch
) internal returns (uint256 boldAmount, uint256 bribeTokenAmount) {
require(_epoch < governance.epoch(),
"BribeInitiative: cannot-claim-for-current-epoch");
...
// Dedaub:
// Seems to be off by 1 second as it calculates the epoch start
// of the next epoch rather than the end of the requested epoch
uint256 epochEnd =
governance.EPOCH_START() + _epoch * governance.EPOCH_DURATION();
uint256 totalVotes =
governance.lqtyToVotes(
totalLQTYAllocation.lqty, epochEnd, totalLQTYAllocation.offset
);
if (totalVotes != 0) {
...
uint256 votes = governance.lqtyToVotes(
lqtyAllocation.lqty, epochEnd, lqtyAllocation.offset);
boldAmount = bribe.boldAmount * votes / totalVotes;
bribeTokenAmount = bribe.bribeTokenAmount * votes / totalVotes;
}
...
}
However, its calculation is the same as the one in Governance::epochStart() which means that the epochEnd gets the value of the timestamp at which the next epoch starts and not when the requested epoch ends. As a result, the offset calculations could be off by 1 sec due to the above property.
When an Initiative gets unregistered it can still have active votes and vetos allocated to it which can be reset later. However, when the users deallocate their LQTY, the Initiative’s onAfterAllocateLQTY hook gets invoked even when this has been unregistered.
The existing Initiative implementations are not directly affected from this behavior, but one might have expected that once an Initiative gets DISABLED no more updates would have been expected to be forwarded from Governance. This could cause issues to Initiatives that depend on their registration status in Governance for their accounting in future versions.
We raise this issue here also for visibility in case this was not the intended behavior for unregistered Initiatives.
Partially resolved
There are two cases in which some of the bribe tokens could end up stuck in the BribeInitiative contract. More specifically:
-
In the
BribeInitiative::_claimBribefunction, the calculation of the bribe shares for a user is susceptible to rounding errors. For example, if thetotalVotesdo not divide exactly the user’s votes or the bribe token amount, then the remainder will be left in the contract since the resulting amount is rounded down. These tokens are not reused in the next epochs nor does a way to extract them exist which makes them locked in the contract. -
If the epoch of a bribe passes with no allocations, the bribe’s funds will not be claimable by anyone, and at the same time there is no way to recover them, so they will remain locked in the contract. Although this does not pose any direct issues to the contract’s operation, ways to recover such funds could exist to rescue them in such a scenario.
OTHER / ADVISORY ISSUES
This section details issues that are not thought to directly affect the functionality of the project, but we recommend considering them.
The new version of the protocol deprecated the average timestamps that previously existed for determining the voting power of an entity and offsets are now used which encodes both the LQTY amounts staked and the staking timestamps. As a result, the Governance::lqtyToVotes function was changed to calculate the voting power based on the distance between offsets.
Governance::lqtyToVotes:276function lqtyToVotes(
uint256 _lqtyAmount,
uint256 _timestamp,
uint256 _offset
) public pure returns (uint256) {
uint256 prod = _lqtyAmount * _timestamp;
return prod > _offset ? prod - _offset : 0;
}
As can be seen above, the function can now be used only with the total amount of LQTY that was used to produce the _offset value with a timestamp greater than or equal to the one that the offset encodes. For example:
-
If a user staked at timestamp an amount of LQTY, then their offset would become .
-
The
lqtyToVotesfor that user cannot be used for any LQTY amount less than because this would makeprod < _offset.
We note this here because, in the previous version, the same function used the average timestamps which allowed getting voting powers with a subset of the total LQTY staked or allocated to an entity.
This functionality is not currently used anywhere in the protocol nor does it seem necessary for it. However, we highlight this difference in case future versions introduce new logic around this function.
In the Governance::_allocateLQTY function, the length checks over the provided arrays have already been performed by the top-level allocateLQTY function. As a result, they can be removed from the internal function since they are also incomplete after the introduction of the offsets as the offset arrays are not checked to have the same length as the rest arrays.
Governance::_allocateLQTY:688function _allocateLQTY(
address[] memory _initiatives,
int256[] memory _deltaLQTYVotes,
int256[] memory _deltaLQTYVetos,
int256[] memory _deltaOffsetVotes,
int256[] memory _deltaOffsetVetos
) internal {
// Dedaub:
// These checks have already been performed by allocateLQTY.
// They are also guaranteed by _resetInitiatives.
// Moreover, they are incomplete as they do not include the new
// _deltaOffsetVotes and _deltaOffsetVetos arrays
require(
_initiatives.length == _deltaLQTYVotes.length &&
_initiatives.length == _deltaLQTYVetos.length,
"Governance: array-length-mismatch"
);
}
After several refactorings in the Governance::allocateLQTY function, the only meaningful values for the _absoluteLQTYVotes and _absoluteLQTYVetos arrays are positive amounts of LQTY to be allocated to Initiatives. This is because all allocations are reset before any (re)allocation.
As a result, these two parameters could be of type uint256 instead of int256 to avoid confusion during pure deallocations. When fully deallocating, users need to provide all the arrays empty except from the _initiativesToReset, compared to the first version in which a deallaction expected a negative value to be provided.
In Governance::registerInitiative function, there are several parts that could be simplified and save gas on operations that are not necessary for that functionality. For example, in order to check whether the Initiative exists or not the value of registeredInitiatives is sufficient. However, the call to getInitiativeState makes unnecessary calls to _snapshotVotesForInitiative even though the Initiative starts with an empty state. The important factor here is that old Initiatives cannot be re-registered.
In addition to that, getInitiativeState also calls _snapshotVotes which updates the global state. However, the same call is also performed by registerInitiative so that it uses the return values from memory. This means that the storage slots are read twice with no additional benefit for the operations performed.
In the Governance::registerInitiative function in order to determine whether the user has sufficient voting power to register a new Initiative Liquity’s Staking V1 contract is queried to return the total user stakes. However, the same value can also be extracted from the sum of the allocatedLQTY and unallocatedLQTY values from the user’s state saving an external call and also some gas.
In the Governance::withdrawLQTY function if a user requests to withdraw more LQTY than the available amount the execution will only revert when trying to subtract the requested amount from the unallocatedLQTY reverting due to an underflow exception. You could have a check earlier in the function so that you could revert the execution with a more representative error message.
In Governance, the getLatestVotingThreshold function returns the voting threshold based on the cached global voting snapshot. However, this snapshot could be out-of-sync if no other operation that updates the global state has been performed in the meantime. You could maybe document this in the function, like in the previous versions, or use a more representative name for the function since the current one could be falsely interpreted as it always returns the most updated voting threshold.
There are some remaining TODOs in the codebase which you may want to take care of before finalizing the codebase.
The code is compiled with Solidity 0.8.24. Version 0.8.24 has no known bugs at the time of writing.
DISCLAIMER
The audited contracts have been analyzed using automated techniques and extensive human inspection in accordance with state-of-the-art practices as of the date of this report. The audit makes no statements or warranties on the security of the code. On its own, it cannot be considered a sufficient assessment of the correctness of the contract. While we have conducted an analysis to the best of our ability, it is our recommendation for high-value contracts to commission several independent audits, a public bug bounty program, as well as continuous security auditing and monitoring through Dedaub Security Suite.
ABOUT DEDAUB
Dedaub offers significant security expertise combined with cutting-edge program analysis technology to secure some of the most prominent protocols in DeFi. The founders, as well as many of Dedaub's auditors, have a strong academic research background together with a real-world hacker mentality to secure code. Protocol blockchain developers hire us for our foundational analysis tools and deep expertise in program analysis, reverse engineering, DeFi exploits, cryptography and financial mathematics.
APPENDIX
Proof of Concept - H1
function test_PoC_H1_BribeMisCalculation() public
vm.warp(block.timestamp + (EPOCH_DURATION)); // We are now at epoch 1
_stakeLQTY(user1, 10e18); // user 1 stakes 10e18
_stakeLQTY(user2, 10e18); // user 2 stakes 10e18
// Deposit 1e18 bribes for bribeInitiative1
_depositBribe(
address(bribeInitiative1), 1e18, 1e18, governance.epoch());
// user 1 allocates 5e18 for bribeInitiative1 and 5e18 for
// bribeInitiative2
_allocateLQTYUser1(5e18, 5e18);
// user 2 allocates 5e18 for bribeInitiative1
_allocateLQTYUser2(5e18);
vm.warp(block.timestamp + (EPOCH_DURATION)); // We are now at epoch 2
// Should be able to claim epoch 1
uint256 prevEpoch = governance.epoch() - 1;
(uint256 bribeTotal, ) = bribeInitiative1.bribeByEpoch(prevEpoch);
console.log(
"Epoch %d: Amount of bribes in bribeInitiative1 for Epoch %d is %e",
governance.epoch(), prevEpoch, bribeTotal );
uint256 boldAmount = _claimBribe(
user1, prevEpoch, prevEpoch, prevEpoch);
console.log(
"Epoch %d: user 1 allocated %d% of the total votes of
bribeInitiative1 and claims %e bribes", governance.epoch(),
_getUserShareOfAllocationAsPercentage(user1 ,prevEpoch),
boldAmount
);
boldAmount = _claimBribe(user2, prevEpoch, prevEpoch, prevEpoch);
console.log(
"Epoch %d: user 2 allocated %d% of the total votes of
bribeInitiative1 and claims %e bribes", governance.epoch(),
_getUserShareOfAllocationAsPercentage(user2 ,prevEpoch),
boldAmount
);
console.log("Epoch %d: Amount of unclaimed bribes is %e",
governance.epoch(), lusd.balanceOf(address(bribeInitiative1)) );
console.log("Epoch %d: Can user 1 claim more bribes for Epoch %d?",
governance.epoch(), prevEpoch);
console.logBool(
!bribeInitiative1.claimedBribeAtEpoch(user1, prevEpoch));
console.log(
"Epoch %d: Can user 2 claim more bribes for Epoch %d?",
governance.epoch(), prevEpoch);
console.logBool(
!bribeInitiative1.claimedBribeAtEpoch(user2, prevEpoch));
}
/**
* Helpers
*/
function _stakeLQTY(address staker, uint256 amount) internal {
vm.startPrank(staker);
address userProxy = governance.deriveUserProxyAddress(staker);
lqty.approve(address(userProxy), amount);
governance.depositLQTY(amount);
vm.stopPrank();
}
function _allocateLQTYUser2(int256 absoluteVoteLQTYAmt) internal {
vm.startPrank(user2);
address[] memory initiativesToReset;
address[] memory initiatives = new address[](1);
initiatives[0] = address(bribeInitiative1);
int256[] memory absoluteVoteLQTY = new int256[](1);
absoluteVoteLQTY[0] = absoluteVoteLQTYAmt;
int256[] memory absoluteVetoLQTY = new int256[](1);
absoluteVetoLQTY[0] = 0;
governance.allocateLQTY(
initiativesToReset, initiatives,
absoluteVoteLQTY, absoluteVetoLQTY
);
vm.stopPrank();
}
function _allocateLQTYUser1(
int256 absoluteVoteLQTYAmt1,
int256 absoluteVoteLQTYAmt2
) internal {
vm.startPrank(user1);
address[] memory initiativesToReset;
address[] memory initiatives = new address[](2);
initiatives[0] = address(bribeInitiative2);
initiatives[1] = address(bribeInitiative1);
int256[] memory absoluteVoteLQTY = new int256[](2);
absoluteVoteLQTY[0] = absoluteVoteLQTYAmt2;
absoluteVoteLQTY[1] = absoluteVoteLQTYAmt1;
int256[] memory absoluteVetoLQTY = new int256[](2);
absoluteVetoLQTY[0] = 0;
absoluteVetoLQTY[1] = 0;
governance.allocateLQTY(
initiativesToReset, initiatives,
absoluteVoteLQTY, absoluteVetoLQTY
);
vm.stopPrank();
}
function _depositBribe(
address _initiative,
uint256 boldAmount,
uint256 bribeAmount,
uint256 epoch
) public {
vm.startPrank(lusdHolder);
lqty.approve(_initiative, boldAmount);
lusd.approve(_initiative, bribeAmount);
BribeInitiative(_initiative).depositBribe(
boldAmount, bribeAmount, epoch);
vm.stopPrank();
}
function _claimBribe(
address claimer,
uint256 epoch,
uint256 prevLQTYAllocationEpoch,
uint256 prevTotalLQTYAllocationEpoch
) public returns (uint256 boldAmount) {
vm.startPrank(claimer);
BribeInitiative.ClaimData[] memory epochs =
new BribeInitiative.ClaimData[](1);
epochs[0].epoch = epoch;
epochs[0].prevLQTYAllocationEpoch = prevLQTYAllocationEpoch;
epochs[0].prevTotalLQTYAllocationEpoch = prevTotalLQTYAllocationEpoch;
(boldAmount,) = bribeInitiative1.claimBribes(epochs);
vm.stopPrank();
}
function _getUserShareOfAllocationAsPercentage(
address user,
uint256 epoch
) internal returns (uint256 userShareOfTotalAllocated) {
(uint256 userLqtyAllocated,) =
bribeInitiative1.lqtyAllocatedByUserAtEpoch(user, epoch);
(uint256 totalLqtyAllocated,) =
bribeInitiative1.totalLQTYAllocatedByEpoch(epoch);
userShareOfTotalAllocated =
(uint256(userLqtyAllocated) * 100) / uint256(totalLqtyAllocated);
}
Proof of Concept - M3
function test_PoC_M3_DepositAndLoseVotingPower() public {
// =================== EPOCH 3 ======================= //
vm.warp(block.timestamp + 2 * EPOCH_DURATION);
// Give some lusd to both users
vm.startPrank(lusdHolder);
lusd.transfer(user, 2e18);
lusd.transfer(user2, 2e18);
vm.stopPrank();
vm.startPrank(user2);
address userProxy2 = governance.deployUserProxy();
lusd.approve(address(governance), 2e18);
lqty.approve(address(userProxy2), 1e18);
// User_2 deposits 1e18 lqty for staking
governance.depositLQTY(1e18);
// User_2 registers an initiative
governance.registerInitiative(baseInitiative);
// =================== EPOCH 4 ======================= //
vm.warp(block.timestamp + EPOCH_DURATION);
// User_2 votes for his initiative with 1e18 lqty
address[] memory initiativesToReset1;
address[] memory initiatives1 = new address[](1);
initiatives1[0] = baseInitiative;
int256[] memory deltaLQTYVotes1 = new int256[](1);
deltaLQTYVotes1[0] = 1e18;
int256[] memory deltaLQTYVetos1 = new int256[](1);
governance.allocateLQTY(
initiativesToReset1, initiatives1,
deltaLQTYVotes1, deltaLQTYVetos1
);
vm.stopPrank();
vm.startPrank(user);
// =================== EPOCH 5 ======================= //
vm.warp(block.timestamp + EPOCH_DURATION);
address userProxy = governance.deployUserProxy();
lusd.approve(address(governance), 2e18);
lqty.approve(address(userProxy), 1_000e18);
// User_1 deposits 1e18 lqty for staking
governance.depositLQTY(1e18);
// =================== EPOCH 6 ======================= //
vm.warp(block.timestamp + EPOCH_DURATION);
// User_1 registers a new initiative
// It works because he has more voting power than the threshold
governance.registerInitiative(baseInitiative2);
// =================== EPOCH 6.5 ======================= //
vm.warp(block.timestamp + EPOCH_DURATION/2);
// User_1 deposits 2e18 lqty for staking
governance.depositLQTY(2e18);
// User_1 registers another initiative
// It fails because the by depositing more lqty the user reduced his
// voting power at EpochStart()
vm.expectRevert("Governance: insufficient-lqty");
governance.registerInitiative(baseInitiative3);
vm.stopPrank();
}
Proof of Concept - M5
function test_PoC_M5_DepositAndLoseVotesForInitiative() public {
// =================== EPOCH 2 ======================= //
vm.warp(block.timestamp + 2*EPOCH_DURATION);
// give usd to user and register initiatives
vm.startPrank(lusdHolder);
lusd.transfer(user, 2e18);
lusd.approve(address(governance), 3e18);
governance.registerInitiative(baseInitiative2);
governance.registerInitiative(baseInitiative3);
vm.stopPrank();
// =================== EPOCH 3 ======================= //
vm.warp(block.timestamp + EPOCH_DURATION);
vm.startPrank(user);
// Deposit 1e18 lqty for staking
address userProxy = governance.deployUserProxy();
lqty.approve(address(userProxy), 1_000e18);
governance.depositLQTY(1e18);
// =================== EPOCH 4 ======================= //
vm.warp(block.timestamp + EPOCH_DURATION);
// Vote for baseInitiative2 with 1e18 lqty
address[] memory initiativesToReset1;
address[] memory initiatives1 = new address[](1);
initiatives1[0] = baseInitiative2;
int256[] memory deltaLQTYVotes1 = new int256[](1);
deltaLQTYVotes1[0] = 1e18;
int256[] memory deltaLQTYVetos1 = new int256[](1);
governance.allocateLQTY(
initiativesToReset1, initiatives1,
deltaLQTYVotes1, deltaLQTYVetos1
);
(IGovernance.InitiativeVoteSnapshot memory initiativeSnapshot,
IGovernance.InitiativeState memory initiativeState,
) = governance.getInitiativeSnapshotAndState(baseInitiative2);
uint256 votesOld = governance.lqtyToVotes(
initiativeState.voteLQTY,
(governance.epochStart() + EPOCH_DURATION),
initiativeState.voteOffset
);
console.log(
"After the first vote, the expected votes to
baseInitiative2 will be: ", votesOld);
// =================== EPOCH 4 (5th day) ======================= //
vm.warp(block.timestamp + 5*EPOCH_DURATION/7);
// Deposit 1e18 lqty for staking (need to reset his votes first)
governance.resetAllocations(initiatives1, false);
governance.depositLQTY(1e18);
// Votes for baseInitiative2 and baseInitiative3 with 1e18 lqty each
address[] memory initiativesToReset2;
address[] memory initiatives2 = new address[](2);
initiatives2[0] = baseInitiative2;
initiatives2[1] = baseInitiative3;
int256[] memory deltaLQTYVotes2 = new int256[](2);
deltaLQTYVotes2[0] = 1e18;
deltaLQTYVotes2[1] = 1e18;
int256[] memory deltaLQTYVetos2 = new int256[](2);
governance.allocateLQTY(
initiativesToReset2, initiatives2,
deltaLQTYVotes2, deltaLQTYVetos2
);
(initiativeSnapshot, initiativeState, ) =
governance.getInitiativeSnapshotAndState(baseInitiative2);
uint256 votesNew = governance.lqtyToVotes(
initiativeState.voteLQTY,
(governance.epochStart() + EPOCH_DURATION),
initiativeState.voteOffset
);
console.log("After the second vote,
the votes to baseInitiative2 will be: ", votesNew);
console.log("The amount of votes for baseInitiative2
is degraded by %s%", (votesOld-votesNew)*100/votesOld);
vm.stopPrank();
}
Proof of Concept - M6
function test_PoC_M6_unregisterInitiativeWhenNotStale() public {
// assuming governance has UNREGISTRATION_AFTER_EPOCHS = 4
vm.startPrank(user);
address userProxy = governance.deployUserProxy();
vm.stopPrank();
vm.startPrank(lusdHolder);
lusd.transfer(user, 1e18);
vm.stopPrank();
vm.startPrank(user);
lusd.approve(address(governance), 1e18);
lqty.approve(address(userProxy), 1e18);
governance.depositLQTY(1e18);
vm.warp(block.timestamp + EPOCH_DURATION + EPOCH_DURATION
); // go to epoch 3, when initiatives can first be registered
governance.registerInitiative(baseInitiative3);
uint256 atEpoch = governance.registeredInitiatives(baseInitiative3);
assertEq(atEpoch, governance.epoch());
vm.warp(block.timestamp + (
governance.UNREGISTRATION_AFTER_EPOCHS()) *
governance.EPOCH_DURATION()
); // go to epoch 7
address[] memory initiatives_to_reset = new address[](0);
address[] memory initiatives = new address[](1);
initiatives[0] = baseInitiative3;
int256[] memory deltaLQTYVotes = new int256[](1);
deltaLQTYVotes[0] = 1e18;
int256[] memory deltaLQTYVetos = new int256[](1);
deltaLQTYVetos[0] = 0;
governance.allocateLQTY(
initiatives_to_reset, initiatives, deltaLQTYVotes, deltaLQTYVetos);
(,, uint256 allocatedLQTY,) = governance.userStates(user);
assertEq(allocatedLQTY, 1e18);
// go to epoch 8
vm.warp(block.timestamp + governance.EPOCH_DURATION());
(IGovernance.InitiativeStatus status,,) =
governance.getInitiativeState(baseInitiative3);
assertEq(
uint8(status), uint8(IGovernance.InitiativeStatus.CLAIMABLE));
address[] memory emptyInitiatives = new address[](0);
int256[] memory emptyDeltaLQTYVotes = new int256[](0);
int256[] memory emptyDeltaLQTYVetos = new int256[](0);
governance.allocateLQTY(
initiatives, emptyInitiatives,
emptyDeltaLQTYVotes, emptyDeltaLQTYVetos
);
(,, allocatedLQTY,) = governance.userStates(user);
assertEq(allocatedLQTY, 0);
// go to epoch 9
vm.warp(block.timestamp + governance.EPOCH_DURATION());
governance.unregisterInitiative(baseInitiative3);
}
