Smart Contract Security Technology for Web3 Projects
BOOK A DEMOStatic Analysis and fuzzing for Project - Pre-deployment and post-deployment
Monitor deployed blockchain projects with high-fidelity surveillance
Decompile and understand contracts without public source or ABI, viewing in Solidity-like format
Smart Contract Security Technology for Web3 Projects
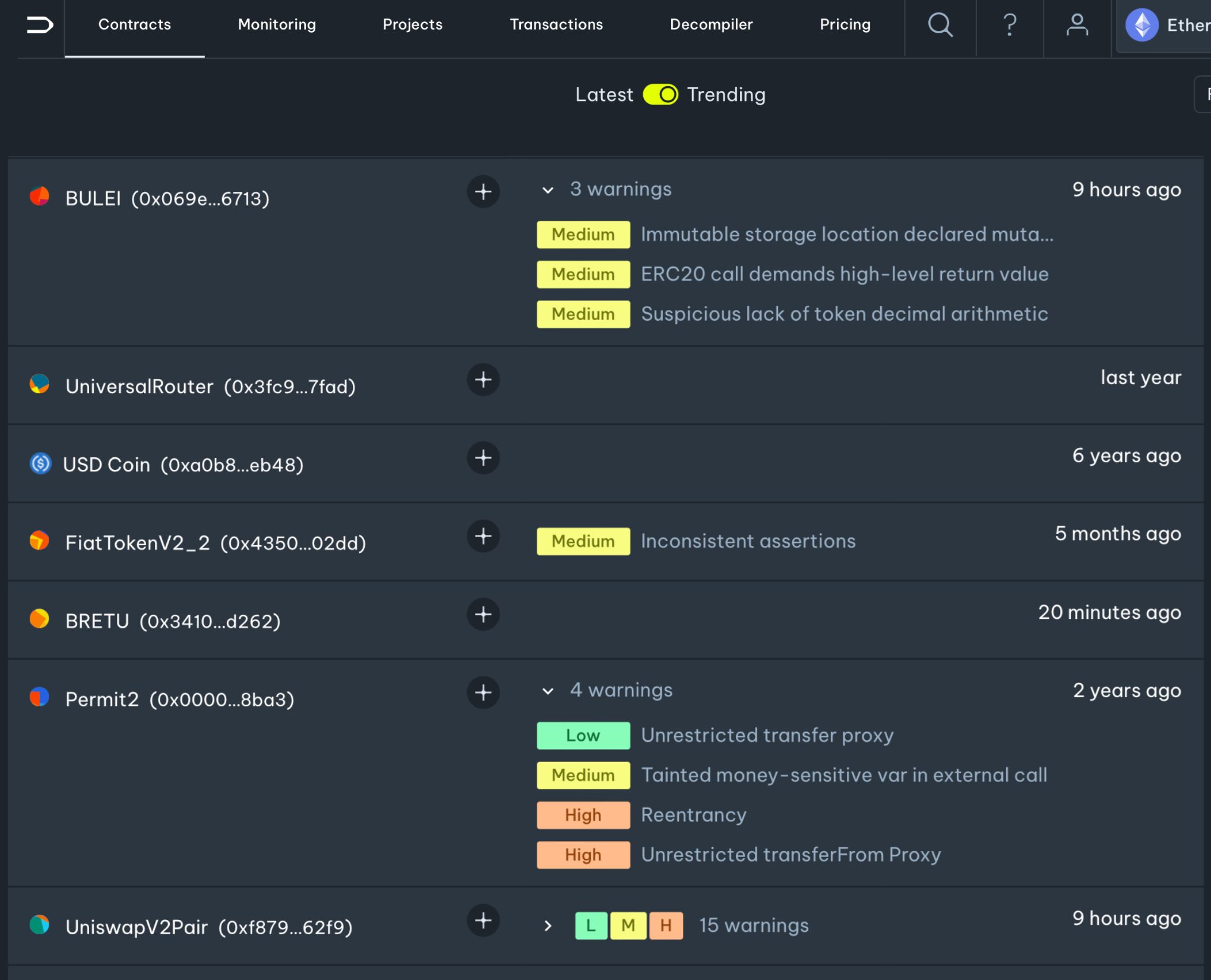
Dedaub Security Suite is a collection of smart contract tools that offers continuous safety checks, combining automated analysis, dynamic monitoring, and statistical learning.
Maintains smart contract explorer decompiled database.
Performs hundreds of custom security analyses.
Monitors state and combines it with code information.
Recognizes deployment of new contracts associated with a protocol.
Preview transactions before executing on-chain.
Filter and search our extensive contracts database using specific criteria.
Smart Contract Security Technology for Web3 Projects
Dedaub Security Suite is a collection of smart contract tools that offers continuous safety checks, combining automated analysis, dynamic monitoring, and statistical learning.
Maintains smart contract explorer decompiled database.
Performs hundreds of custom security analyses.
Monitors state and combines it with code information.
Recognizes deployment of new contracts associated with a protocol.
Preview transactions before executing on-chain.
Filter and search our extensive contracts database using specific criteria.